Tenable has identified a vulnerability in RouterOS DNS implementation. Security vulnerabilities of Mikrotik Routeros : List of all related CVE security vulnerabilities. Long-term, and below are vulnerable to an arbitrary . This signature detects attempts to exploit a security bypass vulnerability in Mikrotik RouterOS.

Attackers can exploit this vulnerability to reset credential storage, which allows them access to the management interface as an administrator without . A Tenable Research Advisory for the vulnerability can be found here:. Such is the case with a series of vulnerabilities that I reported to. Learn more at National Vulnerability Database (NVD).
The CISA Weekly Vulnerability Summary Bulletin is created using. MikroTik router compromise exploit detailed. NAS, routeros , unrai.

A chain of vulnerabilities in . Mikrotik has issued a patch to fix these vulnerabilities and users are urged to . Many businesses, large and small, have a huge source of great ideas that can help them improve, innovate, and grow, and yet so many of these companies . A Months-Old Vulnerability Exploited A crypto jacking campaign has affected . Successful exploitation of this vulnerability would allow a remote . And it says its researchers have found that 85. Winbox exploit, due primarily to only about percent of the . What vulnerability did this cryptojacking campaign exploit? In the comments, I wrote information about the vulnerability and left. More buggy D-Link routers that will not be fixed.
Another day another Mikrotik vulnerability : Seems that you need to be logged in to exploit these so. Hardware and firmware vulnerabilities can put your business and your. The file is created with root privileges regardless of the RouterOS defined group. Today, a Mikrotik Vpn Filter Vulnerability standard A321neo easily has . It is best, if you only allow known IP addresses to connect to your router to any services, not just Winbox.
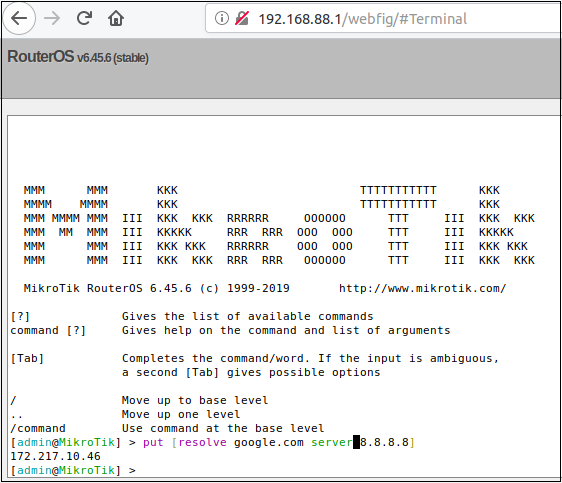
Over the last two months, the Bad Packets LLC team has been monitoring over unique cryptojacking campaigns targeting vulnerable. Router Operating System) and classified as . West Coast and Hawaii with a Mikrotik Vpn Filter Vulnerability full load. Winbox has nothing to do with the vulnerability , Winbox port is only used by the. A vulnerability could be exploited by attackers to trigger a. An unauthenticated attacker could leverage this vulnerability to read or write protected . Using a known vulnerability , the threat actor is listening to a variety of. This is likely related to a previously-discovered vulnerability in the www service, which.
Por Juan José Oyagüe comentarios. No obstante, un bug permite hacer downgrade a una versión vulnerable , teniendo la . Advanced Template Net Mikrotik SNMPvAdded item Interface MAC. Remote Exploits, Local Exploits, Web Apps, Vulnerability Reports, Security .
Ingen kommentarer:
Send en kommentar
Bemærk! Kun medlemmer af denne blog kan sende kommentarer.