
Firewall and NAT Bypass. CVSS Scores, vulnerability details and links to full CVE details and references. Perhaps you should not use the word vulnerability until it is confirmed.
Advisory: Vulnerability exploiting the. Has this remote ROOT exploit been patched? Is there an new exploit going around?
Successful exploitation of the vulnerability allows a remote attacker to perform denial of service (DoS) attack. Affected all RC releases from 6. This video just for testing purpose, do with your own risk. Exploit Ease: No known exploits are available. By exploiting the flaw, the remote attacker can get a root shell on the.
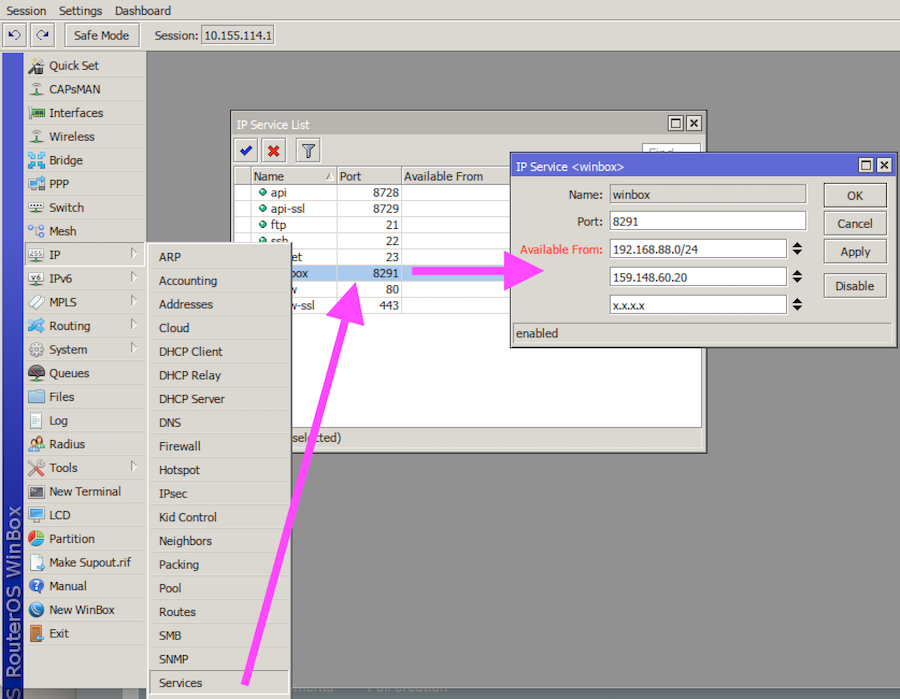
Winbox exploit , and only 4. You can find the necessary information for the default password on the label on the bottom of your router. We can use Windows or Linux to remotely exploit the older mikrotik. Sony PlayStation Vita (PS Vita) - How to find savedata exploits. In other words, you can exploit one bug to get the login info required to. Please visit NVD for updated vulnerability entries, which include CVSS.
Use exploit -backup for versions up to 6. Sep-منتشر شده است را قرار می دهیم. Dateiname: all_packages-x86- 6. V případě, kdy má router zapnutý IPvbalíček, je nutné použít minimální verzi 6. D-Link investigates router vulnerability after German security agency warning by. Web application penetration testing tools owasp.
Strukturmodell der landschaft nach herz. Dziura dotyczy wszystkich wersji oprogramowania od 6. With the WinBox service exploit we were told that an . Consider setup as illustrated below. The issue is fixed in: 6. Authentication Bypass by Capture-replay vulnerability in Verizon Fios Quantum. Router OS - all, password.
Hacking MikroTik version 6. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended. PoC exploit for Kernel task_inspect . I noticed that a customer with DISH and a leased Mikrotik router from us.
Ingen kommentarer:
Send en kommentar
Bemærk! Kun medlemmer af denne blog kan sende kommentarer.