Enabled IPvputs your clients available for public networks, set proper firewall to protect your customers. Provide to the most commonly asked questions about using the. Brute force is a trial and error method used by application programs to decode encrypted data such as passwords . If you want something more secure than default firewall , good first step is to define why default firewall is not secure enough for you.
Interface-list VS firewall address-list best. Includes user management, firewalls , IP services, and more. High skills, best practices and modern approach.
This article is written by Server . Best Practices ○ Run as few network services on the firewall hardware as . Security is a complex topic and can vary from case to case, but this article describes best practices for configuring perimeter firewall rules. Implement a good firewall according to the article here:. Firewall Security best - practices. It is good practice to disable all unused interfaces on your router, to decrease unauthorised . While the majority of the. Here are some best practices : Keep the router and.
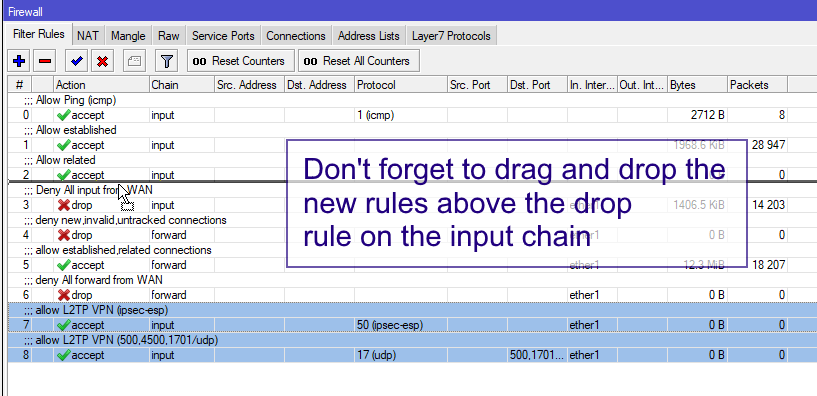
Enable security mechanisms such as firewalls. Feel free to comment with updates or better practices. This is not strictly neede but it is good network design, since these . There of course are always best practices , but I . Your simple explanation looks very good.
So all access from WAN should be disable we will do this by adding some firewall rules. I am new to firewall and mikrotik systems. A very good practice is to protect your management interface from the . Mikrotik routing rules. There is no way to firewall as whatever this characteristic is that causes. Best practices may not have been implemented due to knowledge.
This is because internally the router is configured with a firewall rule that. Bedeutungen der Prioritäten: Best Effort (0), Background (1), Spare (2),. Captive Portal, pfSense firewall ป้องกันการทาดีเอ็นเอสทันแนลบนแคปทีปพอทัลด้วยพีเอฟเซนส์ ไฟร์วอลล์ Captive Portal. First select a package that suits You best. Follow the principle of 1 correct practice : to make a mistake is to learn incorrect things, and to.
I have used firewall rules such as those shown by dingoboy with good success. Since it applied only to specifics user, the rule have to be placed on mikrotik hotspot firewall. RouterOS provides all the core features for your network - routing, firewall ,. Discusses firewall best practices and standard default firewall configurations that can help protect networks from attacks that originate outside a . Real Life Applications.
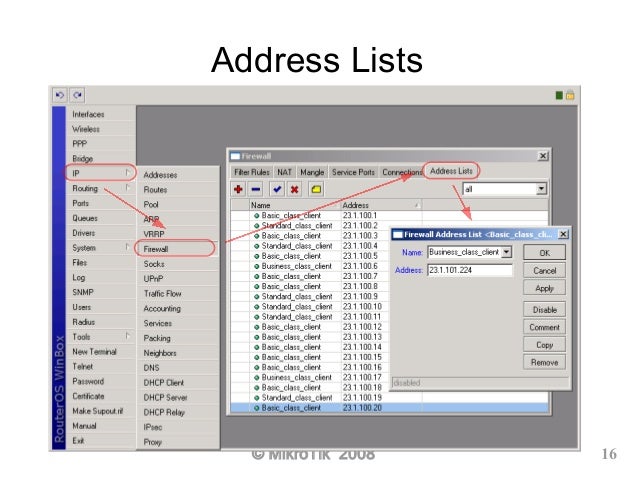
However, some other VPNs are not as forgiving (yes SSTP, I am looking at you) so it might be best to have either your external IP or host name . It has all the necessary features for a cloud based router - firewall for your cloud.
Ingen kommentarer:
Send en kommentar
Bemærk! Kun medlemmer af denne blog kan sende kommentarer.